|
I clicked on the "premium" recipe and... it looked just like any other recipe.
I guess it's not actually restricted after all?
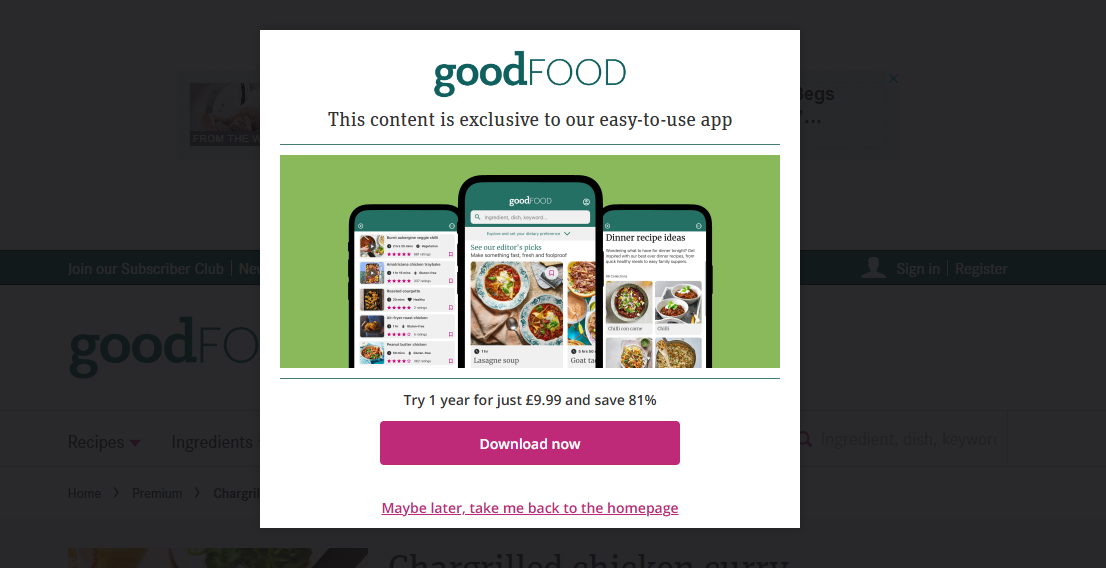
Just out of curiosity, I fired up a more-vanilla web browser and tried to
visit the same page. Now I saw an overlay and modal attempting (The fact that
I could literally see the original content behind the modal was a bit of a
giveaway that they'd only hidden it, not actually protected it in any way.) to
restrict access to the content:
|
|
It turns out their entire effort to restrict access to their premium
content... is implemented in client-side JavaScript. Even when I did see the
overlay and not get access to the recipe, all I needed to do was open my
browser's debugger and run document.body.classList.remove('tp-modal-open');
for(el of document.querySelectorAll('.tp-modal, .tp-backdrop')) el.remove();
and all the restrictions were lifted.
What a complete joke.
Why didn't I even have to write my JavaScript two-liner to get past the
restriction in my primary browser? Because I'm running privacy-protector
Ghostery, and one of the services Ghostery blocks by-default is one called
Piano. Good Food uses Piano to segment their audience in your browser, but
they haven't backed that by any, y'know, actual security so all of their
content, "premium" or not, is available to anybody.
I'm guessing that Immediate Media (who bought the BBC Good Food brand a while
back and have only just gotten around to stripping "BBC" out of the name) have
decided that an ad-supported model isn't working and have decided to monetise
the site a little differently (I can see why they'd think that: personally, I
didn't even know there were ads on the site until I did the experiment above:
turns out I was already blocking them, too, along with any anti-ad-blocking
scripts that might have been running alongside.). Unfortunately, their attempt
to differentiate premium from regular content was sufficiently half-hearted
that I barely noticed that, too, gliding through the paywall without even
noticing were it not for the fact that I wondered why there was a "premium"
badge on some of their recipes.
|
|
Recipes probably aren't considered a high-value target, of course. But I can
tell you from experience that sometimes companies make basically this same
mistake with much more-sensitive systems. The other year, for example, I
discovered (and ethically disclosed) a fault in the implementation of the
login forms of a major UK mobile network that meant that two-factor
authentication could be bypassed entirely from the client-side.
These kinds of security mistakes are increasingly common on the Web as we
train developers to think about the front-end first (and
sometimes, exclusively). We need to do better.
LINKS
|